When we talk about strengthening cyber defenses, we often talk about the key known threats – ransomware, phishing, data breaches and much more. But what happens when you’ve invested in the right solutions to address these threats, and still find that your organization has suffered an attack? Unfortunately, that’s a reality that businesses have increasingly had to face, which is why today, every organization is concerned about how they might be impacted by zero days!
What is a zero-day? It is a vulnerability that’s not known to the vendor or developer of the application, and for this reason, it’s open to exploitation by cyber criminals. Zero-days can and are found in all kinds of applications, whether these are executable Windows/Linux clients, web applications, network protocols, cryptographic algorithms or practically anything else in the digital domain that serves its designed purpose.
The Scale of the Threat
There are approximately 70-80 zero-days disclosed on a daily basis. While some of them present a low level of risk, others can have devastating consequences. An example of the latter is the Operating System zero-day vulnerability which was discovered on the Windows SMB v1 Protocol and affected millions of users worldwide. Or consider the Eternal Blue attack which took advantage of an SMB1 vulnerability. In the time since it was first discovered by cyber criminals, it has wreaked havoc for businesses and users across the globe by attacking users with ransomware, compromising enterprise networks and implanting rootkits.
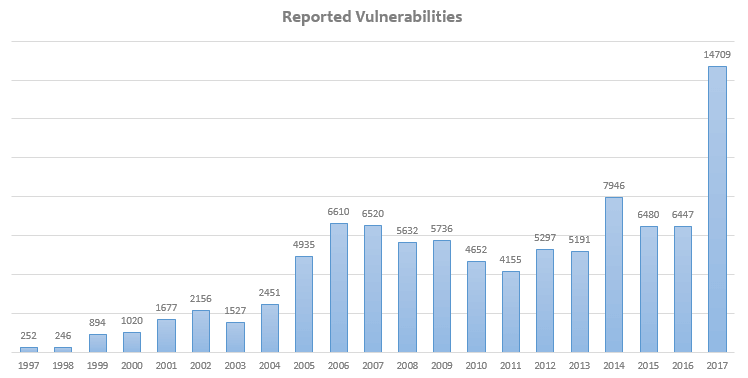
And there’s good reason for businesses to stand up and take note of zero-day threats as over the last 20 years, there’s been a staggering 5,700% increase in the number of vulnerabilities being discovered and exploited annually[1].
Taking Affirmative Action
Typically, organizations only become aware of zero-days after attacks emerge that have exploited the vulnerabilities, or when the threat is made public by security researchers. In either case, this leaves a gap between the announcement of the zero-day and the time to patch systems to protect against the threats – during which the organization remains vulnerable to exploit.
Recognizing these shortcomings, at Help AG, we take a proactive approach. Our R&D team actively hunts for zero-days on various solutions and applications. On uncovering these, they then provide a comprehensive remediation plan to customers that utilize these software solutions so that the threat can be mitigated before it is exploited by malicious users.
Unmatched Expertise
The reason we have been far more successful at this activity than any other security organizations in the region is that our R&D team performs their zero-day research by first carefully selecting the solutions that are most relevant and extensively used by regional businesses. They then carefully analyze them in a fully equipped virtualized lab environment to discover critical bugs. This R&D lab consists of a complex environment to emulate various products and services such as enterprise domain controllers, VoIP networks, network segregation, application layer security protocols, network level security protocols as well as web services where the vulnerability hunting takes place.
So far, Help AG has discovered over 85+ zero-days across many widely utilized applications and operating systems, including Linux, CMS solutions, thick clients and more. An example is the vulnerability on the CMS solution, Joomla Core, which our R&D team managed to uncover using SQL Injection. If this vulnerability was instead found by a malicious user, it could have been used to attack around 1.8 million websites[2]. We found that using an SQL Injection[3] against the user note list section of the authenticated CMS solution enabled us to exploit it and gain access to the database. Had this been known to attackers, they could have used it to retrieve the content of the database, escalate their privileges or compromise other accounts within the database.
Furthermore, as part of their continuous research, our R&D team utilizes dedicated servers to perform fuzzing and exploitation on platforms on a continuous basis with the intent of helping the IT community to stay safe and secure. The team also uses the lab to test and verify the latest threats. This allows them to simulate the impact of attacks within a controlled environment and create a working exploit in a controlled infrastructure. The working exploit can then be used during our penetration testing against our customers’ IT environments to make sure that they are checked and assessed against the very latest threats.
While you might have believed that your best defense against zero-day threats is to be rapidly reactive, it’s clear that Help AG’s proactive approach is far more effective. So, if you’re looking for a way to protect your critical IT assets against not just known, but also unknown threats, don’t hesitate to get in touch with us!
References:
[1] https://www.welivesecurity.com/2018/02/05/vulnerabilities-reached-historic-peak-2017/
[2] https://websitesetup.org/popular-cms/
[3] https://www.owasp.org/index.php/SQL_injection





