Help AG provides comprehensive XIoT security services that go beyond traditional IoT, covering OT, IIoT, IoMT, BMS, and more to protect your critical infrastructure and connected devices.
We cater to a wide range of advanced XIoT security needs
Reduce the risk of cyber-attacks with proactive threat detection and response.
Minimize downtime and ensure continuous operations.
Prevent costly breaches and operational disruptions.
Reduce the risk of cyber-attacks with proactive threat detection and response.
Minimize downtime and ensure continuous operations.
Prevent costly breaches and
operational disruptions.
We partner with leading vendors to deliver cutting-edge XIoT security solutions and services.
We partner with leading vendors to deliver cutting-edge malware analysis solutions:
At Help AG, we provide a suite of specialized assessments to enhance your OT & IoT platforms security and ensure your peace of mind.
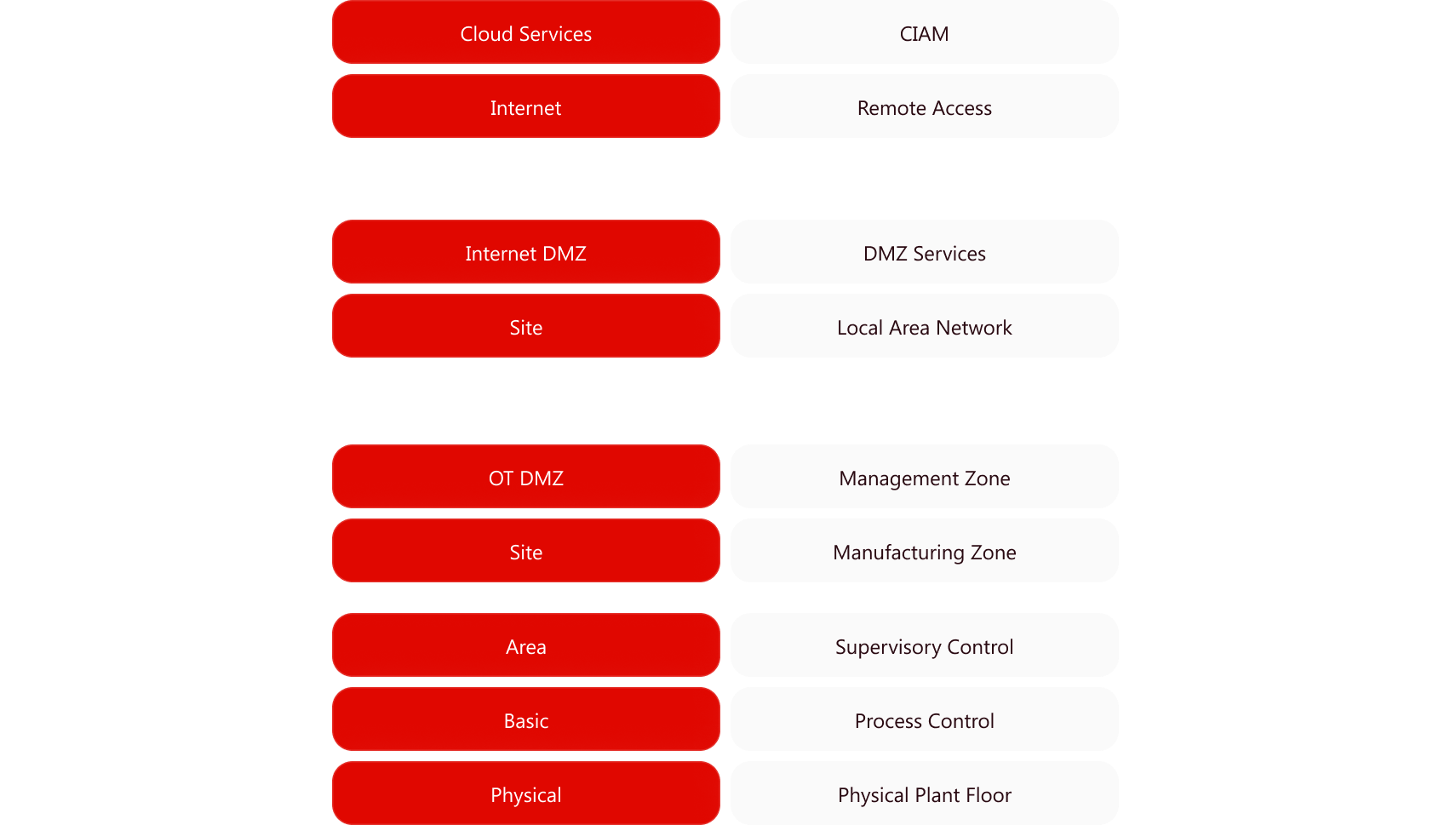
Securing operational technology isn’t optional anymore. Our OT reviews are tailored for industrial control systems, aligning with IEC 62443 standards and regional directives like the Saudi NCA. From segmentation to protocol inspection, we assess how well your critical infrastructure is shielded from cyber-physical attacks.
Security starts with sound design. Our architectural reviews evaluate your network, system, and application architecture against zero-trust principles, segmentation strategies, and threat models. We uncover systemic risks, misaligned trust boundaries, and legacy dependencies — and provide recommendations that modernize and harden your environment.
Get under the hood of your security stack. We perform detailed configuration reviews across key infrastructure components (firewalls, endpoint platforms, VPNs, proxies, etc.) to ensure they align with industry best practices and your organizational threat profile. Misconfigured systems are often the low-hanging fruit for attackers — we help you take them off the menu.
Investigate and identify signs of security breaches or compromises within your OT environment.
Examine system configurations to detect and rectify security weaknesses and misconfigurations.
Analyze the design of your security infrastructure to ensure it meets best practices and is resilient against threats.
Identify gaps between current OT security measures and industry standards, recommending improvements.
Evaluate vulnerabilities and potential attack paths in OT systems to enhance security.



Speak to our cybersecurity experts to safeguard
your infrastructure.
securing customers’ digital journey & fortifying cyber defence.
offering an end-to-end portfolio of services that are catered to securing devices.
where creativity meets cutting-edge innovation to drive transformative solutions.
protecting your cloud infrastructure with cutting-edge security solutions.
insights and analysis on the latest trends & technologies.
stay updated with our latest news, press releases, & more.
in-depth research and analysis on key cybersecurity topics.
watch & learn from our insightful video gallery
critical updates and alerts on emerging threats.
comprehensive guides and technical documents.
Real-world examples of our solutions in action across industries.
Real feedback and impact from our customers' experiences.
These are the zero-day vulnerabilities discovered.