In the evolving landscape of cybercrime, Business Email Compromise (BEC) schemes have been known for posing persistent threat to organizations worldwide. Over the years, Help AG has been continuously tracking various such campaigns targeting multiple countries in the Middle East. Recently, we have discovered a campaign targeting organizations in the United Arab Emirates. In this particular campaign, the scammers masquerade themselves as government agencies to persuasively deceive and defraud their victims.
In this blogpost, we expose their attack patterns by uncovering their tactics and techniques. We at Help AG, urge the public to be more vigilant, and proactively employ security measures to battle these threats.
Understanding BEC Scams
Business Email Compromise (BEC) scams involve criminals leveraging sophisticated social engineering techniques and often impersonating executives, high ranking officials and/or trusted partners. The primary goal is to trick potential victims into divulging sensitive information, initiating unauthorized financial transactions, and/or spreading malware to create a backdoor for persistence.
Typical tactics and techniques used for BEC scams include, but are not limited to –
- Spearphishing- In this method, scammers conduct meticulous research on their targets, gathering any available information on the organization and the employees who could be ideal victims. With this information, they craft highly sophisticated emails that emphasize on authority, urgency, or threat that manipulate specific targets into taking action.
- Fake Domains or Typosquats – Scammers often use similar domain names to trusted government agencies or partners to dupe their victims, Unfortunately, some victims fail to perform due diligence in confirming the legitimacy of sender email addresses.
- Brand or Company Impersonation – This tactic involves manipulating victims with legitimate logos, publicly available document templates and details such as authority addresses, and department information.
Unmasking Operation Lustrous Deception
Here below are the tactics and techniques that scammers used in this recent BEC scam campaign.
Spearphishing The scammers unleashed their well-crafted phishing emails by impersonating a government -theme campaign. They leveraged ongoing local projects and imposed a sense of urgency to entice victims into engaging with it.
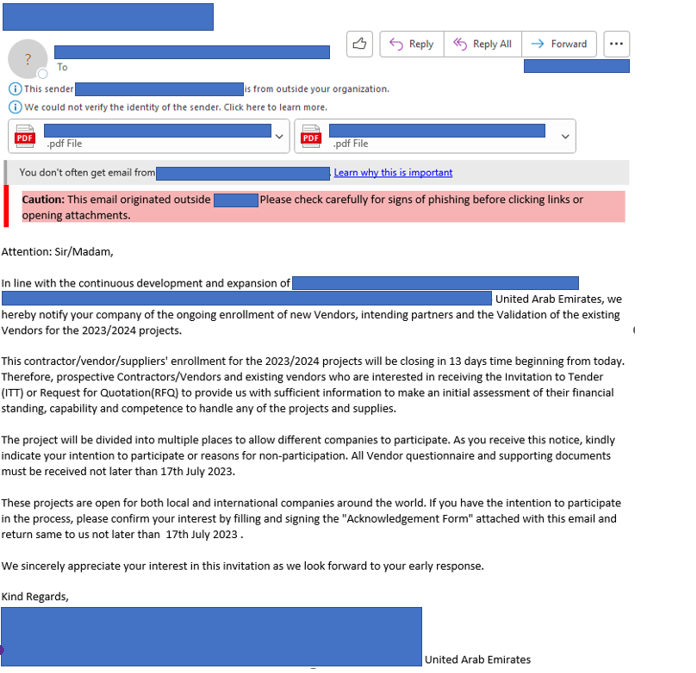
Image: The screenshot displays a phishing email masquerading as an authentic communication from a UAE government organization. The email is designed with such precision that it appears entirely legitimate, making it easy for an unsuspecting victim to fall prey to its deceptive tactics.
Use of Fake Domain or Typosquats
Help AG has discovered multiple fake domains registered by scammers. These fake domains have been used to make the campaign appear as if it was coming from a legitimate sender(s).
This information has been shared with our customers as part of the regular Cyber Intelligence advisories, to raise awareness, enhance cybersecurity measures and ultimately stay vigilant against these deceptive tactics.
Brand or Company Impersonation
Help AG has also discovered the scammers deliberately impersonating government agencies by using brand names logos as well as issuing fake receipts, stamps, and documents. This alarming discovery is crucial for our customers to be aware of the extent of deception employed by these attackers, and hence the need to verify all official communications to protect against potential threats.

Image – This document depicts a form sent to targets, bearing the authentic letterhead of a UAE organization. The form requests recipients to fill in personal details, and its convincing appearance can easily deceive victims who fail to verify the email source.
Help AG Analysis
Further analysis and investigation of this recent BEC scam campaign are as follows –
Help AG has traced this campaign to a Nigerian threat group that we are aware of. This group is known for employing this BEC scheme, which includes but is not limited to:
- Crafting spear phishing emails by impersonating government brand-theme campaigns, masquerading as new or ongoing local project requirements.
- Primarily targeting the organization’s vendor management department, which oversees the tender registration process.
- Persuading victims to transfer a certain amount as part of the tender registration requirements, promising the amount is refundable.
- Help AG has also discovered that the scammers have leveraged publicly accessible legitimate documents, a slightly modified them to impersonate the government agency and enhanced the credibility of their campaign.
- In addition, Help AG has uncovered several fake domains registered by the scammers. These fake domains contain government brand names, intentionally designed to appear. This technique is known as typosquatting.
- Help AG’s thorough analysis has deemed this particular campaign a financially motivated fraud, preying on victim’s ignorance to extort funds.
- Further investigation by Help AG has revealed that similar campaigns have been repeatedly used by scammers since April 2021, targeting various organizations. Help AG’s research has discovered more than 500 unique domain names associated with the same threat group, targeting various organizations worldwide, including the UAE. This Cyber Threat Intelligence (CTI) information has been communicated as part of our regular CTI updates to our customers and OSINT (Open Source Intelligence) partners.
Recommendations
Help AG is committed to continuously monitoring and tracking cybersecurity threats, exposing scammers’ tactics and techniques, and promoting public vigilance. Below is a list of recommendations that could help in protecting organizations from similar threats.
- Ensure all systems and software are up to date with the latest patches.
- Avoid opening emails, clicking links, or downloading attachments from unknown or suspicious sources.
- Regularly conduct security awareness training for your employees to ensure they can recognize phishing emails and are aware of the tactics used by scammers.
- Monitor newly registered domains similar to your company’s to detect potential typosquatting or combosquatting activities.
- Implement sophisticated email filtering solutions that can help identify and quarantine phishing emails.
- Encourage employees to promptly report any suspicious emails or incidents.
- Deploy Domain-based Message Authentication, Reporting & Conformance (DMARC) to authenticate emails and prevent spoofing.
Important Note: Help AG proactively shares all cyber threat intelligence information through our thorough analysis and investigation of this campaign with our customers.







