In an era where traditional security falls short, Help AG leads the defense against digital threats with a 360-degree managed cyber defense portfolio.
As a managed security service provider, our services address skill shortages, meet compliance demands, and boost cyber resilience – keeping organizations ahead in a fast-evolving digital landscape.
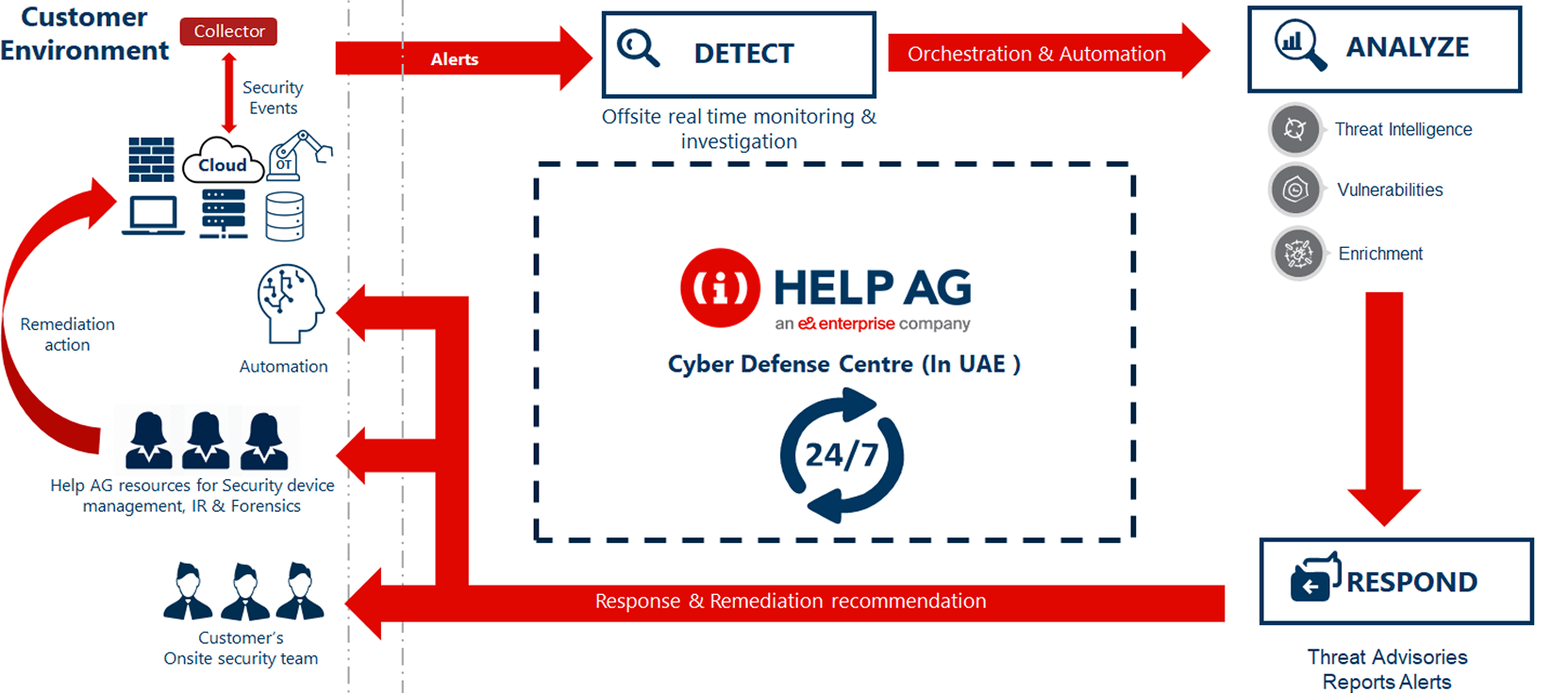
Our Managed Detection & Response (MDR) service provides round-the-clock threat monitoring, analysis, and incident response. By leveraging advanced analytics and expert analysts, we rapidly detect and contain cyber threats before they impact your business. MDR ensures real-time visibility and a proactive security posture across your digital environment.
Managed Threat Intelligence delivers curated, contextualized threat insights to help organizations stay ahead of adversaries. We monitor global threat landscapes and analyze emerging TTPs (Tactics, Techniques, and Procedures) to inform defensive strategies, support decision-making, and strengthen your security architecture.
Our Managed Endpoint Detection and Response (Managed EDR) monitors endpoints in real-time, identifying abnormal behavior and enabling immediate containment. It empowers security teams with visibility into endpoint activity, root cause analysis, and rapid remediation capabilities, helping mitigate ransomware, malware, and insider threats.
Managed Network Detection & Response (Managed NDR) safeguards your network by detecting lateral movement, command-and-control communications, and network anomalies. With deep packet inspection and behavior analytics, we provide full-spectrum threat visibility and help stop threats before they spread.
CTEM is a proactive program that continuously assesses your environment to identify exposures and prioritize remediation. We simulate attacker behavior to find weak points in your digital estate, ensuring you stay ahead of vulnerabilities, misconfigurations, and gaps in defenses—reducing your overall attack surface.
Improve your organization’s security posture by training technical & business stakeholders to ensure swift, informed decision-making, minimize damage & maintain trust. during a cyber security incident. Workforce readiness service includes simulated attacks, scenarios and role-based training modules tailored for continuous improvement.
Digital Risk Rating provides a continuous assessment of your organization’s risk exposure across public-facing assets & digital footprint. Services expand to identifying vulnerabilities, assessing third party risk, and enabling proactive risk management. This helps prioritize remediation of vulnerabilities and guides strategic investments in security.
We simulate real-world attacks and validate whether your security controls detect and prevent them. This ensures your security investments in firewalls, EDR, and other tools are working as expected.
Our DRP service helps monitor the dark web, social media, and underground forums for data leaks, brand abuse, and impersonation attempts. It enables quick takedown actions and alerts you before threats escalate.
We manage web proxies to control user access to internet content, prevent data exfiltration, and block malicious sites. This service adds a layer of outbound threat defense and helps enforce acceptable use policies.
Automated Response accelerates threat containment by triggering predefined actions—such as isolating endpoints or disabling accounts—based on real-time threat identification & intelligence. This reduces response time; limits damage and frees up security teams to focus on RCA & handling complex threats.
We apply machine learning and artificial intelligence to analyze massive volumes of security data, detecting anomalies and predicting threats with high accuracy. This analytical layer enhances detection, reduces false positives, and uncovers hidden threats across the environment.
A compromise assessment uses forensic tools and expert analysis to determine whether your environment has been infiltrated. We uncover hidden threats, dormant malware, and backdoors, and present full incident timeline and mitigation roadmap of identified threats.
DFIR provides a structured, expert-led response to security incidents—ranging from ransomware to insider threats. We identify the root cause, assess the scope of impact, and restore operations while preserving evidence for legal or compliance requirements.
Our Managed Security Controls service delivers end-to-end administration, monitoring, and optimization of your foundational security technologies—including firewalls, endpoint protection, Active Directory, email security, and web proxies. We ensure each layer of your security stack is configured according to best practices, continuously tuned for evolving threats, and fully integrated with your broader cyber defense strategy. By offloading the operational burden to our expert team, your organization benefits from improved resilience, reduced risk, and consistently enforced security policies—all without the overhead of managing it in-house.
We configure, manage, and monitor firewall policies to block unauthorized access while ensuring business continuity. Our experts tune your firewalls based on threat intel and compliance standard
We setup, fine-tune & manage security for your web application using this service to protect your websites & applications against incoming attacks. This service enhances application security, reduces downtime, and helps maintain compliance with data protection regulations.
Endpoint Detection & Response tools continuously monitor endpoints to detect suspicious behavior and automate response actions. We ensure policy tuning, visibility, and integrations to maximize threat coverage.
We manage web proxies to control user access to internet content, prevent data exfiltration, and block malicious sites. This service adds a layer of outbound threat defense and helps enforce acceptable use policies.
Email remains the top threat vector. We deploy & manage advanced email security controls including spam filtering, malware detection, and impersonation protection to safeguard users and sensitive data.
Get continuous security event monitoring to safeguard your infrastructure around the clock.
Reduce breach risks by proactively identifying and addressing vulnerabilities.nt.
Manage predictable, budgeted expenses, avoiding unexpected cybersecurity costs.
Tap into seasoned cybersecurity professionals whenever needed.
Avoid penalties by meeting industry regulations and standards with expert guidance.
Eliminate the need to find, train, or retain security personnel, allowing for more efficient operations.
Leverage cutting-edge cybersecurity technologies without incurring high capital expenses.
Get continuous security event monitoring to safeguard your infrastructure around the clock.
Reduce breach risks by proactively identifying and addressing vulnerabilities.nt.
Manage predictable, budgeted expenses, avoiding unexpected cybersecurity costs.
Tap into seasoned cybersecurity professionals whenever needed.
Avoid penalties by meeting industry regulations and standards with expert guidance.
Eliminate the need to find, train, or retain security personnel, allowing for more efficient operations.
Leverage cutting-edge cybersecurity technologies without incurring high capital expenses.
Help AG’s Managed Security Services leverage our state-of-the-art Cyber Defense Centers in the UAE and KSA.
We prioritize addressing your business's most critical risks, ensuring our solutions deliver measurable security outcomes while adapting to evolving cyber threats.
With over 450+ use cases aligned with the MITRE ATT&CK framework, our Threat Content Framework ensures precise detection and deep visibility across a wide range of attack vectors, offering comprehensive coverage of evolving threats.
At the core of our threat detection capabilities is Unicorn, our in-house developed threat detection content management platform.
Unicorn centralizes threat content management, automatically pushing and distributing use cases across customers. This automation extends to use case management and tuning, ensuring consistently low false positive rates and reducing operational burden.
With robust Digital Forensics and Incident Response (DFIR) capabilities, we ensure swift detection, analysis, and containment of threats, backed by Threat Detection Assurance that constantly validates the efficacy of your defenses.
We offer both on-premise SOC and cloud-based SOC solutions, providing real-time monitoring, detection, and response tailored to your infrastructure, whether it’s traditional, cloud, or hybrid.
Through intelligent automation, we streamline threat detection and response, minimizing false positives and enhancing operational efficiency, ensuring faster, more accurate incident management.
Our SOC Maturity Assessment framework ensures continuous evolution of your security operations center, improving your security posture and adapting to new cyber threats.
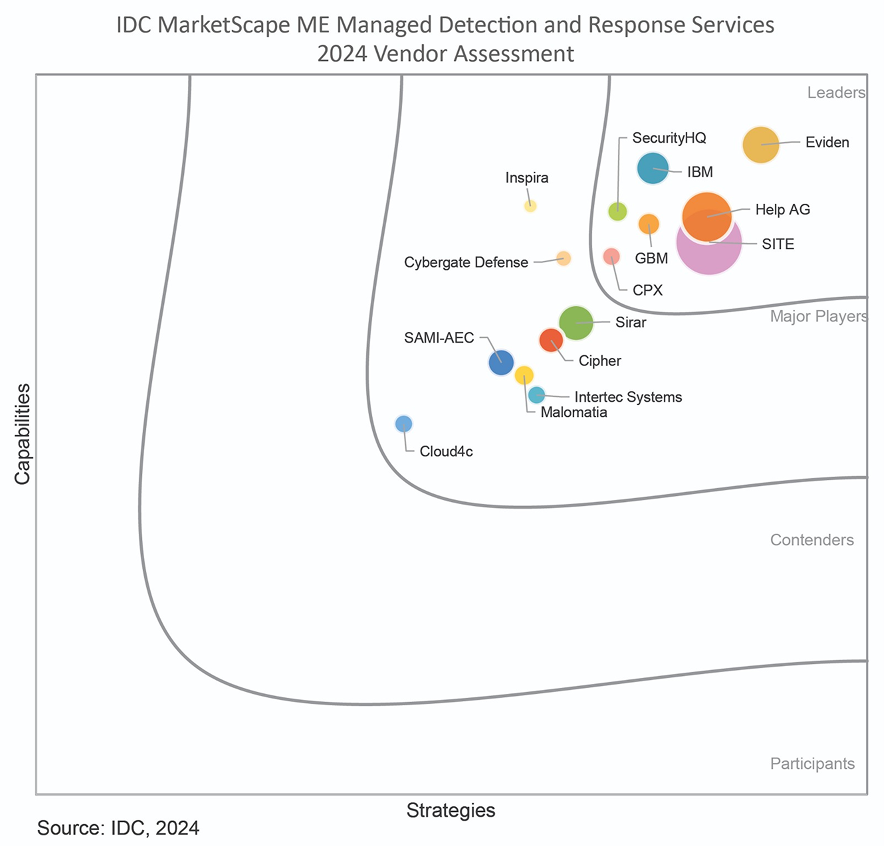
IDC MarketScape vendor analysis model is designed to provide an overview of the competitive fitness of ICT suppliers in a given market. The research methodology utilizes a rigorous scoring methodology based on both qualitative and quantitative criteria that results in a single graphical illustration of each vendor’s position within a given market. The Capabilities score measures vendor product, go-to-market and business execution in the short-term. The Strategy score measures alignment of vendor strategies with customer requirements in a 3-5-year timeframe. Vendor market share is represented by the size of the circles.
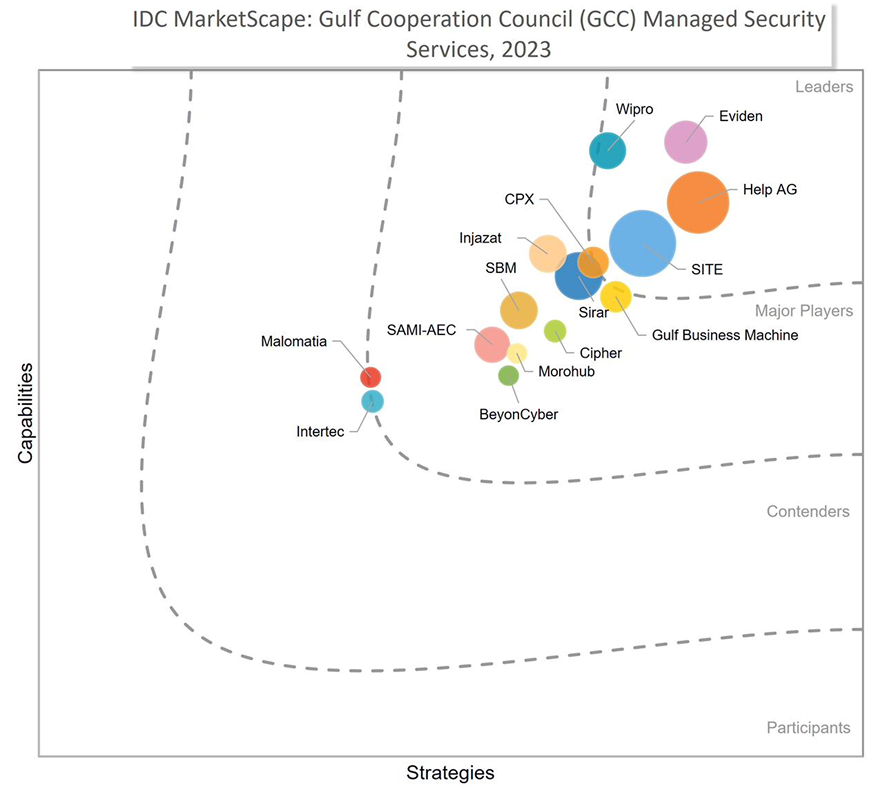
IDC MarketScape vendor analysis model is designed to provide an overview of the competitive fitness of ICT suppliers in a given market. The research methodology utilizes a rigorous scoring methodology based on both qualitative and quantitative criteria that results in a single graphical illustration of each vendor’s position within a given market. The Capabilities score measures vendor product, go-to-market and business execution in the short-term. The Strategy score measures alignment of vendor strategies with customer requirements in a 3-5-year timeframe. Vendor market share is represented by the size of the icons.
Security starts with sound design. Our architectural reviews evaluate your network, system, and application architecture against zero-trust principles, segmentation strategies, and threat models. We uncover systemic risks, misaligned trust boundaries, and legacy dependencies — and provide recommendations that modernize and harden your environment.
Get under the hood of your security stack. We perform detailed configuration reviews across key infrastructure components (firewalls, endpoint platforms, VPNs, proxies, etc.) to ensure they align with industry best practices and your organizational threat profile. Misconfigured systems are often the low-hanging fruit for attackers — we help you take them off the menu.
Is your SOC built to outpace today’s threats? Help AG’s SOC maturity assessment evaluates people, processes, and technology across your detection and response capabilities. Using globally recognized frameworks like MITRE D3FEND and NIST CSF, we help elevate your SOC into a strategic, intelligence-driven defense hub.
Ransomware doesn’t knock — it crashes in. We simulate ransomware attack paths, evaluate your detection and response readiness, and benchmark your defenses against MITRE ATT&CK for ransomware. You’ll walk away with a heatmap of vulnerabilities, mitigation strategies, and an action plan for real-world preparedness.
Is there a threat actor already inside? Our compromise assessment uses threat hunting, endpoint forensics, and behavioral analytics to determine whether your systems have been breached — and if so, to what extent. This is not just an investigation — it's a digital health check powered by real-world threat intel.




Speak to our cybersecurity experts to safeguard
your infrastructure.
securing customers’ digital journey & fortifying cyber defence.
offering an end-to-end portfolio of services that are catered to securing devices.
where creativity meets cutting-edge innovation to drive transformative solutions.
protecting your cloud infrastructure with cutting-edge security solutions.
insights and analysis on the latest trends & technologies.
stay updated with our latest news, press releases, & more.
in-depth research and analysis on key cybersecurity topics.
watch & learn from our insightful video gallery
critical updates and alerts on emerging threats.
comprehensive guides and technical documents.
Real-world examples of our solutions in action across industries.
Real feedback and impact from our customers' experiences.
These are the zero-day vulnerabilities discovered.