Top Drivers To Make You Rethink Your Cybersecurity Strategy

Year after year, cybersecurity teams across the globe are faced with new challenges to tackle. There has never been a dull moment for cybersecurity professionals in combating the increase and advancement of cybercrime, and this will remain the case for the upcoming years and decades.
The increased adoption of technology in everyday life and in business, as well as the dynamic changes to how we conduct business, have expanded the attack service and changed the security perimeter, thus requiring organizations to rethink their IT security strategy.
We will explore below some of the top modern drivers that will need attention in the upcoming period.
Increased Adoption of Remote/Hybrid Workforce
Since the pandemic, the workplace has changed forever – there has been a significant increase in the number of employees working remotely or in a hybrid model, introducing additional risks due to employees’ utilization of their own uncontrolled home networks.
Employers have coped with this change by adopting cloud security technologies, tightening policies, providing awareness, enhancing endpoint defenses, and enforcing stringent controls over authorization and authentication mechanisms, to name a few.
Rise of Ransomware
We have seen an unprecedented increase in ransomware attacks in the past couple of years, with global cybercrime damage predicted to hit $265 billion by 2031, up from $20 billion in 2021 as per a recent BCI publication. The key to mitigating the risks of ransomware is combining many security aspects such as adopting a Zero Trust approach, employee education, anti-malware tools, hardening the endpoints, implementing secure backup solutions, practicing effective monitoring, and having incident response plans in place.
Cybersecurity Skills Shortage
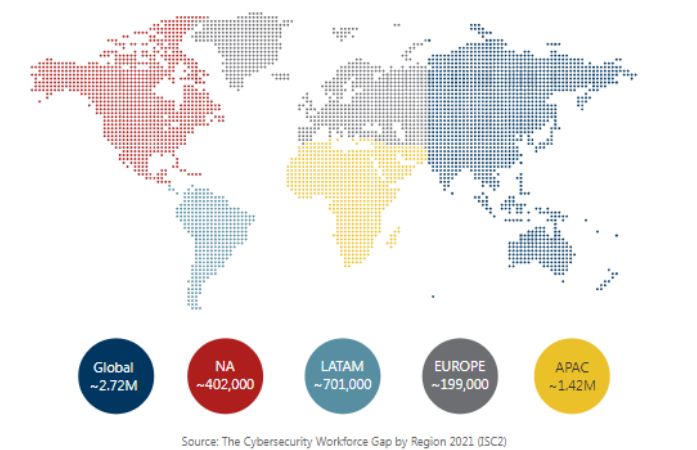
It continues to be a challenge for organizations across all sectors to hire and retain talent in the cybersecurity space, with an estimated shortage of 2.7 million resources in 2021 globally as per a recent ISC2 cybersecurity workforce study.
Organizations are overcoming this challenge by creating a better work culture to attract the new generation of cybersecurity professionals, collaborating with universities to train the next generation, and identifying potential candidates that do not shy away from challenges. Cross-organizational transfer and competitive benefits are also used to retain talent.
Advance In Phishing Attacks
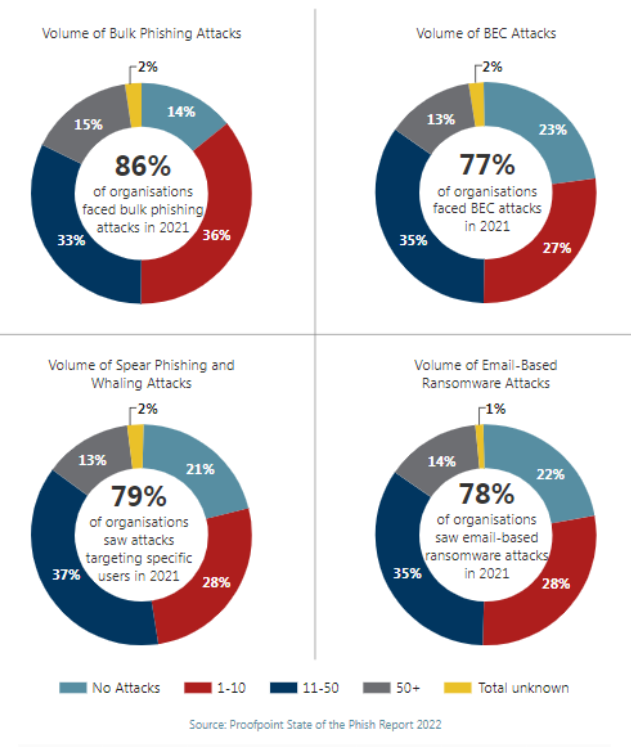
Phishing still remains one of the preferred easy-to-use attack vectors utilized by cybercriminals worldwide. 82% of breaches continue to rely on the human element as a key driver, according to the 2022 Verizon DBI Report, wherein these attacks are split between phishing and pretexting.
Even though the click rate has declined over the past year due to organizations’ efforts to educate their users, we simply cannot ignore that even a single phished user can cause significant harm to the entire organization. In addition to continuous education, there are several technologies and solutions adopted by enterprises to mitigate phishing risks, such as web filtering, encryption, email security, and spam filtering.
Moreover, organizations need to strengthen their security posture to remain cyber resilient against a number of challenges that have come about in this era of digital transformation, and introduced by the increased adoption of IoT devices, the continuous shift of data and applications to the cloud and the increased usage of mobile devices to conduct everyday business.
Do’s |
Don’ts |
| Check the correctness of the recipients’ email addresses before sending an email, as errors could result in undesirable consequences. | Click on links in emails that you are suspecting to be malicious. |
| Inspect but don’t click. Hover over the link in an email before clicking on it to validate if it is legit. | Fall for sudden urgent emails coming from your superior or colleague and share details without confirming with them. |
| Report any malicious-looking emails to your cybersecurity help desk function immediately. | Trust the sender’s display name without a confirmation. |
| Look for typos and bad grammar, these are indications of illegitimate emails. | Divulge personal or company confidential information to any party. |
| Keep an eye out for unfamiliar attachment file types and check for files with double extension. | Respond or reply to spam in any way. |
| Report any system slowness or device overheat to your IT support team. | Install any untrusted software on your company provided assets. |
| Report any virus detections in the system that are not automatically cleaned by the anti-virus to your IT support team. | Keep your device unmonitored/unattended while working from a public area. |
| Restart your laptop at the end of each working day or on weekends at the least. | Enter your system’s password and credentials when someone is watching. |
| Report any outdated anti-virus programs to your IT support team. | Attempt to install pirated software. |
| Report any suspected security incident to your cybersecurity help desk function. | Attempt jailbreaking or rooting your company provided phone. |





